image source: www.zerohedge.com
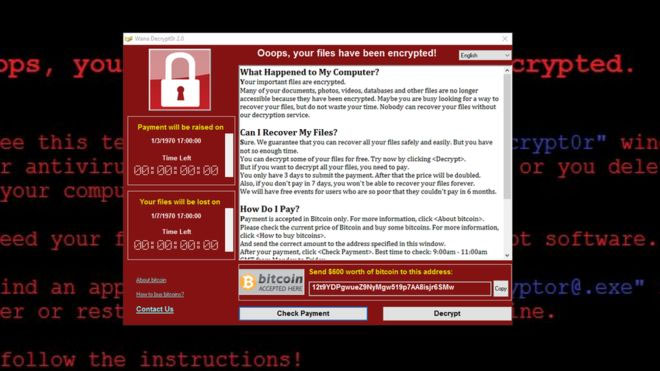
Early morning last Saturday, a ransomware called ‘WannaCry’ wrecked havoc infecting 74,000 PCs in 99 countries exploiting a security vulnerability found within older version of Microsoft Windows® operating system demanding ransom to be paid to release encrypted files within computer systems.
Who were hit by this unprecedented attack?
Europol says it was unprecedented in scale and this is a major outbreak since a malware attack in 2009 and the victims were no minor entities. At the time of writing UK‘s National Health Services empowering the backbone of publicly funded healthcare system is crippled with the country’s Cyber Security Agency “working around the clock” according to its head to restore services across 45 NHS services within the country. In addition to the NHS in UK, Russia‘s Health & Interior Ministry, Domestic Banks, State owned Railway, Second Largest Mobile phone operator in all were infected making Russia the hardest hit out of the European continent.
According to BBC, In Spain, a number of large firms – including telecoms giant Telefonica, power firm Iberdrola and utility provider Gas Natural – were also struck, with reports that staff at the firms were told to turn off their computers. People tweeted photos of affected computers including a local railway ticket machine in Germany and a university computer lab in Italy. France’s carmaker Renault was forced to stop production at a number of sites. Portugal Telecom, the US delivery company FedEx and a local authority in Sweden were also affected. All these organizations employ thousands of IT administrators and invest Billions of Dollars in annual budgets to safeguard critical IT infrastructure; so, what went wrong?
The evolution of ransomware: How a nuisance turned into a business
The malware in concern is a type of a worm which distributes itself from one PC to another using stealthy attack mechanism and is identified as ransomware solely because it asks for a ransom to be paid to release the files to its rightful owner. The payment is also requested in the form of ‘Bitcoin’ a digital cryptocurrency which is impossible to track and source.
The infected file is usually sent across as an email attachment with harmless and curious heading that may impersonate a purchase order, payment receipt or a airway bill that requires urgent attention. Driven by curiosity, the user is tempted to open the compressed email attachment which contains the infected file (cleverly renamed to impersonate a word document) which in turn encrypts the data in hard drive within minutes and demands the user to pay up or lose the important files. In the meantime the program uses the infected PC to infect local users as well as to send emails impersonating the local user to infect PCs globally.
Most concerning, is the recent finding that now readily distributable ransomware kits is available from $39 from the dark web enabling any person to develop this into a business enterprise to extort money from unsuspecting users. The latest outbreak is a marriage between ransomware and a operating system fault opening up an another mutation.
But I Paid for an Anti-Virus to Protect Me
Since initial discovery, Ransomware started a battle in between security researchers and malware creators which led to the evolution of both platforms. Anti-Virus creators deployed Advance Treat Protection (ATP) to prevent attachment files to access malware deployments and many IT administrators blocked compressed email attachments through organizational firewalls. In turn ransomware was sent in using just word documents attached to the email that requested the users to download a macro file to properly see the attachment which led to a malicious payload delivered by macros. IT administrators countered this by sending an organization wide email requesting the users not to allow any document to download macro files. It has become a ‘game of cat and mouse’ at the expense of security and overall organizational productivity.
Anti-Viruses come in few flavors. If your antivirus is based on signatures (i.e. updates which inform the virus guard on how to react to a virus when infected) there is a high probability that your protection is limited. Make sure you anti-virus is equipped with behavior analysis components as well to anticipate and react to an active threat rather than rely on an instruction set.
Preventive Measures to Protect from Ransomware
- Invest in genuine software to ensure that critical system updates are available on time and no hack tool is used to activate product.
- Update your operating system to the latest supported version by the developer. If your application software is dependent on the operating system version and is costly or impossible to migrate switch to an embedded version with extended lifetime support.
- Make sure your signature based anti-virus is up to date. Actively refer to Gartner and Forrester reports to select a industry recommended product.
- Invest in a behavior based anti-virus product that dynamically analyses program execution, patches vulnerabilities, provides visibility at the case of an attack on attack vectors.
- Make sure your firewall is updated to the latest version.
- If possible ask you security vendor to deploy a solution where you firewall, signature based anti-virus and behavior based anti-virus work in unison to protect your devices from evolving threat landscape.
- Implement a backup plan and delegate responsibilities to your IT staff based on a schedule.
- Invest in a backup solution that keeps offsite backups. Keep in mind that a backup is not a replication. If you make a synchronized copy to a local file share, a mapped NAS drive, popular cloud file share such as One Drive, Google Drive or Dropbox they too will be encrypted when the ransomware hits. A RDX Backup is an ideal solution.
- Educate your users regularly to not to open up attachments from unknown users or known users acting suspiciously.
For the time being it would be a continuous battle in between the good and the bad. Its time we take our network and device security seriously to stay ahead of the curve.
Comments
[insert_php]comments_template( ”, true ); [/insert_php]




